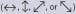Optoelectronic Applications: Quantum Cryptography - Alice and Bob beef up security
Talk to anyone in the field of quantum cryptography and the conversation inevitably turns to Alice, Bob, and Eve. Wanting to keep their communications private, Alice (the sender) and Bob (the receiver) decide to set up a quantum encryption system that uses a stream of single photons to transfer a unique cryptographic key between them. Their goal is to foil the attempts of Eve (the “eavesdropper”) to hack into the system and intercept their message, thus disrupting the security of the transaction.
In essence, quantum cryptography works by exploiting a basic law of quantum physics: the process of observing a quantum object changes that object forever. If Eve attempts to eavesdrop on Bob and Alice, her efforts to read the data stream will alter it because the photon is converted to electrical energy as it is measured, which destroys it. To keep her presence a secret, she must then generate a new quantum message to Bob, guessing at the digital values of the photons, which in turn creates errors in the string of values used in the encryption key. Thus, quantum cryptography works not so much by directly protecting the data but by detecting whether an eavesdropper is trying to access the data.
“The idea is not that Alice sends her actual information to Bob,” said Danna Rosenberg, a physicist at Los Alamos National Laboratory (LANL; Los Alamos, NM) who is working with noise-free detectors to extend the capabilities of quantum key distribution (QKD), the most widely used form of quantum cryptography. “They create a secret shared key, a random string of zeros and ones, and then they put their original data in binary form and mix it with the shared key. So it’s not just that they know someone is eavesdropping; rather, they can test the system prior to sending the important data.”
The basic concepts of quantum cryptography have been around since the 1970s, and some historians maintain its roots go back even further, to the formulation of Heisenberg’s uncertainty principle in 1927 (see “The Heisenberg principle and BB84”).1,2 But commercial implementations of this technology are still in the early stages. In 2002, id Quantique (Geneva, Switzerland) began marketing single-photon detectors and random-number generators and now offers systems integration as well. MagiQ Technologies (New York, NY) introduced the first commercial QKD system in 2003. In 2004, BBN Technologies (Cambridge, MA) began operating the DARPA-funded Quantum Network, which has been running continuously ever since, testing the viability of several QC technologies and techniques.3
“Metaphorically speaking, it is like the early days of the steam engine, when people had lots of ideas of how you might build one,” said Chip Elliott, principal engineer at BBN. “But it eventually became clear what the better way was to do it. At BBN, we are trying one of everything to determine things like, are there advantages to using entanglement, or is it more trouble than it’s worth?”
Demonstration projects such as the DARPA Quantum Network, the European SECOQC project (“Development of a Global Network for Security Communication based on Quantum Cryptography,” expected to go live next year), and the recently formed Australian consortium QCV-IDI (Quantum Communications Victoria-Industry Development Initiative) are going a long way toward helping quantum cryptography move out of the lab and into the “real world.” Commercial point-to-point secure links using QKD-based encryption techniques have been launched by id Quantique and MagiQ, and several large Japanese corporations, including Mitsubishi, NEC and Toshiba, have product-oriented programs for QKD system development. At this point, early adopters include the military, financial institutions, and telecom providers, all of which are actively testing QKD systems for securing data transactions.
Less is more
Still, some technical hurdles remain before quantum cryptography will become more broadly adopted. The key is in the photons—the fewer there are, the less chance Eve has of nabbing those that contain important data. Quantum key distribution systems transmit the keys (derived from random numbers) one photon at a time in a polarized state. If intercepted by Eve, the state of the photon will change and an error will be detected at the receiving end. The keys are transmitted on a different line than the data and at a much slower rate, although even 1000 bit/s is fast enough to send the keys and even change them one or more times per second.
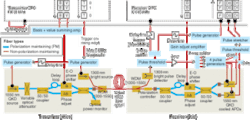
Setting up a QKD system requires much more than getting two parties to agree upon and exchange an encryption key, however. A typical configuration involves the integration of multiple components and services, from the fiberoptic network that facilitates the Alice/Bob link and the communications protocols that facilitate the encryption to the lasers and photodetectors that send and receive the photons (see Fig. 1).
Most of the QKD systems available today use highly attenuated laser pulses from a 1550-nm diode-laser source. These lasers are readily available, relatively cost-effective, and easy to integrate with fiberoptic networks that use the same kinds of lasers at the same wavelength. While it is generally acknowledged that single-photon laser sources would simplify QKD system design and improve the distances at which these systems can operate—currently about 120 km maximum, after which the photons become too weak to maintain the necessary level of security—many in this industry believe that attenuated lasers will continue to dominate the field.
“With the current state of technology, attenuated laser pulses are sufficient, and my guess is that for the next few years all the commercial systems are going to use attenuated lasers,” said Gregoire Ribordy, founder and CEO of id Quantique. “Of course if we had a perfect single-photon source we could go longer distances because most of the time with attenuated lasers you are basically sending an empty pulse and the detectors can still pick up noise, which limits the distance. But at this stage, the complexity of these sources is way too high compared to the benefits they bring.”
Ribordy and others believe that the real limiting factor in quantum cryptography is the lack of high-quality single-photon detectors. According to many quantum cryptography experts, avalanche photodiodes (APDs) offer the best promise for meeting this need. Princeton Lightwave (Cranbury, NJ), for example, has developed an indium gallium arsenide/indium phosphide (InGaAs/InP)-based single-photon APD (based upon technology licensed from IBM) for use in quantum cryptography. According to the company, the detector outperforms photomultiplier tubes and commercial linear-mode APDs used in QKD and other photon-counting applications.4
Similarly, BBN Technologies recently demonstrated a single-photon detector designed for standard telecom fibers; laboratory trials have confirmed continuous operation at 100 million pulses/s, and the technology could be scalable to 10 billion pulses/s (20 times faster than current single-photon detectors) and beyond. The compact, rack-mounted detector system uses packaging and cooling technology developed at the National Institute of Standards and Technology (NIST; Boulder, CO) that efficiently couples the superconducting detector to a standard telecom fiber and allows operation at a temperature of approximately 3 K without using liquid cryogens.
In a slightly different approach, researchers from LANL, NIST, and Albion College (Albion, MI) are using new superconducting transition-edge sensors (TESs) to distribute cryptographic key material at 1550 nm through 50 km of optical fiber. Unlike single-photon APDs, TESs detect photons by measuring minute temperature increases in a superconducting material caused by the absorption of individual photons.
“The TESs provide significantly higher detection efficiencies and lower dark-count rates than those of typical avalanche photodiodes,” Rosenberg said. “The high efficiency and low probability of dark counts, coupled with the relatively short recovery time of TESs, should permit higher secret key transmission rates at longer distances than APD-based systems.”
Using the current system, the LANL/NIST team has shown a maximum transmission distance for data with bright pulse and electrical synchronization of 83 and 138 km, respectively. More sophisticated methods of filtering photons might someday allow users to send quantum keys securely over distances in excess of 270 km, compared to the current record of 122 km.
Entangled and spooky
In addition to ongoing development of single-photon laser sources and photodetectors, a number of other next-generation quantum cryptography approaches are being investigated. Some companies and research groups are focusing on wireless and ground-to-satellite applications.5 Others such as MagiQ are working with commercial partners to demonstrate novel ways to overcome the distance and point-to-point limitations of current quantum cryptography systems. At the OFC/NFOEC conference last March, MagiQ and Verizon reported that they had successfully bridged two separate spans of 80 km of commercial fiber by cascading several MagiQ QPN 7505 devices. In addition, they demonstrated that quantum keys can be mixed with other optical signals on a single strand of fiber, which can reduce the cost of these systems.
“Using single photons, the signal gets too faint and you can’t regenerate it because of its quantum nature,” said Bob Gelfond, founder and CEO of MagiQ. “But using our cascaded system, you can get around this issue. Other future technologies, such as quantum repeaters, will effectively overcome this hurdle as well, but they are a few years off.”
Other next-generation approaches to QKD include chaotic synchronization, differential phase-shift keying, and quantum decoys.6, 7 Among the most advanced of these is photon entanglement and the related concept of “spooky action.” In this scenario, a laser pump directs a stream of photons at a nonlinear crystal (see Fig. 2). In this scheme the incoming photons stimulate the crystal, which then generates and ejects twin photons in opposite directions but with the same quantum states. While photon entanglement offers advantages for quantum cryptography in the long term, from a commercial perspective key distribution using standard 1550‑nm lasers and improved detectors will continue to dominate this field for at least a few more years.
“One of our questions (at BBN) is does entanglement give you better security than weak lasers pulses? Elliott said. “While we found that it is a little better, it is also a lot slower. So we’ve decided we like the attenuated laser pulses.”
REFERENCES
1. J. Ouellette, The Industrial Physicist (December 2004).
2. D. Gottesman, H.K. Lo, Physics Today 53(11) (November 2000).
3. B. Schweber, EDN, Dec. 16, 2005, p. 41.
4. M. Itzler, Compound Semiconductor (March 2006).
5. W. Knight, New Scientist (June 2005).
6. K. Greene, MIT Tech. Review (Jan. 24, 2006).
7. K. Greene, MIT Tech. Review (March 3, 2006).
The Heisenberg principle and BB84
The Heisenberg uncertainty principle dictates that it is fundamentally impossible to know the exact values of complementary variables such as a particle’s momentum and its position. In quantum cryptography, this concept translates into the use of nonorthogonal quantum states to encode information. Given a single photon in one of four possible polarizations
Various communications protocols used in quantum key distribution exploit this scenario; the most popular is BB84, invented by Charles Bennett of IBM (Armonk, NY) and Gilles Brassard of the Université de Montréal in 1984. The BB84 protocol uses pulses of polarized light in a stream of single photons (one photon per pulse) to encode and decode data and transfer a cryptographic key between two parties. Other QKD protocols include B92, proposed by Charles Bennett of IBM in 1992, which uses only two nonorthogonal states.
Kathy Kincade | Contributing Editor
Kathy Kincade is the founding editor of BioOptics World and a veteran reporter on optical technologies for biomedicine. She also served as the editor-in-chief of DrBicuspid.com, a web portal for dental professionals.