CHRISTOPHER CHUNNILALL and TIM SPILLER
Quantum key distribution (QKD) is an ultrasecure communication method that uses quantum states of light to communicate between two distant parties (‘Alice’ and ‘Bob’), enabling them to create a secret shared encryption key that can be used to transmit and receive messages (see Fig. 1).
To keep electronic information—such as biometric and financial data—secure, it is encrypted before being transferred between parties. Simply, this involves jumbling it up in a particular way so that it can only be unjumbled by someone who has the key. When Alice sends an encrypted message to Bob, they both need the same key to encrypt and decrypt it. Simply stated, QKD is a unique way of creating and securely sharing a key between Alice and Bob.
Key security
Data encoded using current algorithmic key distribution schemes is vulnerable to being cracked with mathematical insight, powerful computers, or future quantum computers. Work is underway on new mathematical algorithms (“post-quantum” cryptography) that will not be vulnerable. However, it will be very hard to provide security against all possible future quantum computer cryptanalysis.
QKD techniques encode the key using a physical process, not an algorithmic one. As such, key security depends on the physical performance of the QKD system at the time of key creation.
Given a theoretical model for the system, which is built on a set of assumptions about the abilities and performance of the hardware, QKD can be proven unconditionally secure. However, any differences between the actual physical system and the theoretical model could introduce vulnerabilities in the security that could be exploited. Physical characterization is therefore essential to ensure that the hardware is operating as intended. The parameters that go into the theoretical model need to be measured, as well as the effectiveness of measures implemented to nullify hacking attacks.1
How does QKD work?
Quantum key distribution takes advantage of a fundamental aspect of quantum mechanics: observing a system changes its quantum state. The key is encoded into the quantum states or pulses of light. If a third party—Eve—tries to copy the quantum state in transit, she cannot avoid introducing changes to the light that can be detected when it is received. But if the stream of quantum light signals has been received unchanged, Bob and Alice know that they—and only they—have the key. They can then begin sending encrypted messages with confidence.
In one example of QKD, Alice sends out a string of single photons (elementary particles of light) encoded to represent a bit—a ‘1’ or a ‘0’. Not all will arrive at Bob. Some will be lost in the optical fiber medium, and some may be stolen. That doesn’t matter, however—the key is just created from the photons that are received. Bob uses an open channel to tell Alice that he received the photons in position 1, 5, 7, and so on, and those are used to create the key.
If Eve steals the photons, they won’t arrive and won’t form part of the key, so are useless to her. If she measures them and tries to send a duplicate, quantum physics guarantees that she will sometimes change the state of the photons, making it clear that they have been tampered with. At this point, a new key is created. So, it is physically impossible for Eve to steal the key.
Alice’s transmitter is a pulsed photon source (the highly attenuated output from a laser) that modulates the encoding property of the photons. For optical fiber communications, this may typically be the phase of the photons, or the time slot in which they are transmitted. A random number generator selects the state to be encoded at random.
At Bob’s end, there are single-photon detectors. For example, if phase-encoding is used, an interference measurement is performed, with detectors at each output port of the interferometer. The phase is determined from knowing which detector receives the photon.
The evolution of QKD
Commercially viable QKD transmitters and receivers are available—however, they are physically large and expensive, and only suitable for very high-value security applications. The aspiration of the industry is to address these size, weight, and power (SWaP) limitations, to deliver practical quantum-secured communications that will open broader markets for consumers, commerce, and government. This has been one of the driving goals of the Quantum Communications Hub (www.quantumcommshub.net) since it was established by the UK government in 2014 as part of the UK National Quantum Technologies Programme (http://uknqt.epsrc.ac.uk). The Hub is led by the University of York (York, England), and is a collaboration of eight universities, the UK National Physical Laboratory (NPL; Teddington, England), and numerous industrial partners.
A major step towards SWaP-saving is to engineer QKD on affordable chips, such as those that will fit into a smartphone. The physics is proven, but the challenge is developing small-enough devices.
For transmitters, photon sources at chip-scale have been successfully developed using light sources with filters to control production of single photons. These provide workable devices for current commercial QKD. However, further photonics challenges remain, particularly around chip-scale entangled photon generation for alternative approaches to QKD.
Detectors are more challenging since materials sensitive enough to detect single photons are bulky. The best current detector materials are superconducting—requiring significant cooling apparatus. However, detector size is less of an immediate problem since early QKD would likely involve a secure end-user location—such as a bank or government department—that could accommodate a bulkier detector. But the long-term goal is smaller detectors so that laptops can communicate directly with each other, pointing towards semiconductor devices.
Developing and testing QKD
QKD systems are being developed in many countries, most notably in Austria, Canada, China, Japan, South Korea, Switzerland, the U.S., as well as the UK.
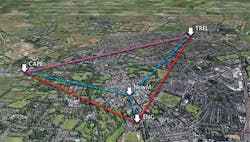
A driving goal of the Quantum Communications Hub creating the UK’s first quantum network, the UKQN, is providing a place to test and demonstrate new technologies and highlight useful applications of QKD. The UKQN comprises multinode fiber-optic networks in Bristol and Cambridge, with connections being established between them, and also from Cambridge to BT Labs at Adastral Park near Ipswich, England (see Fig. 2).In recent years, Hub industrial partners ADVA, BT, and Toshiba demonstrated that 200 gigabit-per-second (Gbit/s) data, encrypted with quantum keys, can be sent over 100 km of fiber—with one channel in the same fiber being used to establish the quantum keys. This is progressing well towards the first high-speed real-world deployment of quantum-based network security in the UK.
Meanwhile, NPL is working with the Hub, industrial developers, and other national measurement institutes to establish accurate, robust measurements to verify the security of QKD keys.2 Measurements must be performed at the single-photon level and with low jitter, since QKD systems can operate at clock rates above 1 GHz. Single-photon detectors and sources used to respectively characterize QKD transmitters and receivers must be calibrated to the International System of Units (SI).
Even though quantum communications products are now available, the lack of agreed-upon standards for testing device performance is limiting end-user confidence and slowing potential industry uptake of these systems. The European Telecommunications Standards Institute (ETSI; Sophia-Antipolis, France) Industry Specification Group on QKD (ETSI ISG-QKD) is working to provide the documented standards and procedures that are required for the development of an assurance framework for these technologies.3 NPL led the drafting of the first ETSI Group Specification to document measurement protocols for testing QKD components.
The future of QKD
Currently the most practical and commercially advanced QKD systems use single photons that are created by attenuating laser pulses. Originally developed as modules fitting into 19-in. racks, chip-scale prototypes have been recently developed, offering low SWaP consumption and the potential for integration into consumer electronics (see Fig. 3).4Other methods of implementing QKD are being rapidly developed, including those based on encoding information into the phase of multiphoton pulses, as well as systems based on entangled photons. These approaches have advantages and disadvantages with respect to the current approach, and it is anticipated that they will all find their role in a future quantum-enabled security network.
Considerable research is also going into extending the range over which QKD can be used. Fiber links limit the point-to-point range of QKD to a few hundred kilometers because of the attenuation loss as photons propagate through optical fiber. And while performing QKD over ‘lit’ fiber carrying standard communications traffic further reduces the transmission distance due to increased noise, distances around 100 km have been demonstrated under these conditions.
Setting up trusted nodes is the short-term answer to long-distance secure communication. This involves detecting keys and then re-encoding quantum states, meaning that the nodes must be completely secure to maintain QKD’s guarantee that no one has eavesdropped. A longer-term solution is quantum repeater technology that involves stretching out high-quality quantum entanglement over very long distances. However, this technology is still a way off, as quantum processing and quantum memories are required. Nonetheless, it is hoped that significant headway will be made towards entanglement distribution and quantum repeater stations during Phase 2 of the UK National Quantum Technologies Programme, which starts in 2019 and runs for five years.
Global QKD could ultimately be achieved by distributing keys via satellites, as there is less photon loss and decoherence experienced in the clear atmosphere and in space. This can also bring QKD to locations where it would be costly, unfeasible, or not secure enough to create fiber links. This field has been stimulated by a recent demonstrator system, and various test missions are in the planning stage.5 Satellite QKD is another priority area for the UK’s quantum program over the next five years.
These new approaches will also require a calibration and assurance process, and the ETSI ISG-QKD recently prepared a report surveying some of the new protocols and the physical parameters that will need to be characterized.3
Technology push, industry pull
Although QKD is a proven technology, the next steps involve further SWaP-saving improvements and demonstrating network scalability. Only by engaging with industry and demonstrating successful applications of QKD using test facilities such as the UKQN and working with technical and cyber security standards bodies such as ETSI and the UK’s National Cyber Security Centre (London, England) will the physical specifications and security protocols be established to encourage end-user investment and allow QKD systems to proliferate.
Early adopters are likely to be government and financial institutions, whose high-value communications and trading habits can be lucrative targets for sophisticated hackers. But in the end, necessity may drive uptake of QKD. The advent of quantum computing—another technology that uses information encoded into the states of quantum devices and systems—will lead to the ability to quickly crack current algorithmic encryption codes. Post-quantum algorithms are being actively researched. However, as proof that these codes will always be uncrackable is likely to be very difficult, “future-proof” secure systems may need to combine both QKD and post-quantum algorithms.
REFERENCES
1. See http://bit.ly/quantumphotonics1.
2. See http://bit.ly/quantumphotonics2.
3. See http://bit.ly/quantumphotonics3.
4. P. Sibson et al., Nat. Commun., 8, 13984 (2017).
5. See http://bit.ly/quantumphotonics4.
Christopher Chunnilall is a senior scientist in the Quantum Metrology Institute at the National Physical Laboratory, Teddington, England; e-mail: [email protected]; www.npl.co.uk/quantum-metrology-institute, and Tim Spiller is director of the York Centre for Quantum Technologies, director of the UK Quantum Communications Hub, and a professor at the University of York, York, England; www.york.ac.uk/physics/people/spiller.
![FIGURE 1. In this example of an optical-fiber-based QKD system, the quantum (open) channel is in blue (black). SPD0 and SPD1 are single-photon detectors. Each bit is encoded by a pair of pulses—in phase (antiphase) pulses are separated by nλ ([n+½]λ), where n is an integer and λ is the wavelength of the light, and lead to a detection at SPD0 (SPD1). If Eve tries to measure this separation and resend a copy, she will sometimes change it (see rightmost pair of pulses) and cause a detection in the ‘wrong’ detector. FIGURE 1. In this example of an optical-fiber-based QKD system, the quantum (open) channel is in blue (black). SPD0 and SPD1 are single-photon detectors. Each bit is encoded by a pair of pulses—in phase (antiphase) pulses are separated by nλ ([n+½]λ), where n is an integer and λ is the wavelength of the light, and lead to a detection at SPD0 (SPD1). If Eve tries to measure this separation and resend a copy, she will sometimes change it (see rightmost pair of pulses) and cause a detection in the ‘wrong’ detector.](https://img.laserfocusworld.com/files/base/ebm/lfw/image/2019/01/1901lfw_chu_f1.png?auto=format,compress&fit=max&q=45&w=250&width=250)